7 Plenary Session | Robust Machine Learning Algorithms and Systems for Detection and Mitigation of Adversarial Attacks and Anomalies: Proceedings of a Workshop | The National Academies Press
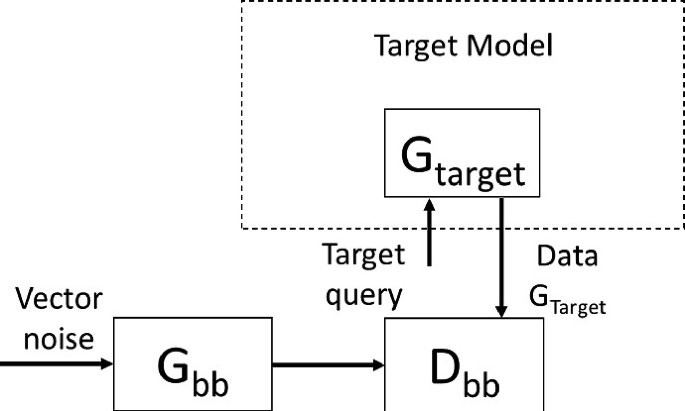
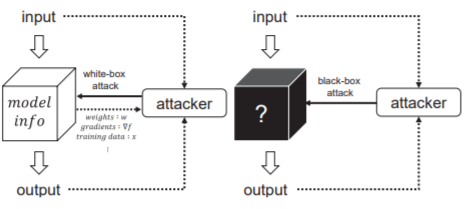
Comprehensive Analysis of Privacy in Black-Box and White-Box Inference Attacks Against Generative Adversarial Network | SpringerLink

python - which attack in cleverhans is grey box attack and which is white/black box attack in cleverhans library? - Stack Overflow

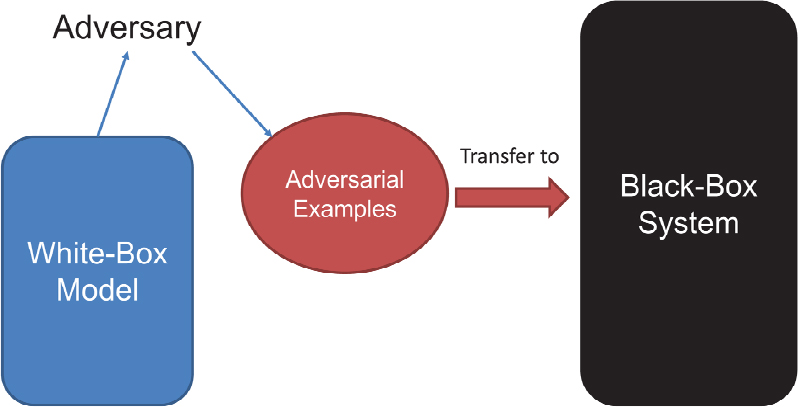
Overview of the transferability hypothesis from a white‐box attack on a... | Download Scientific Diagram
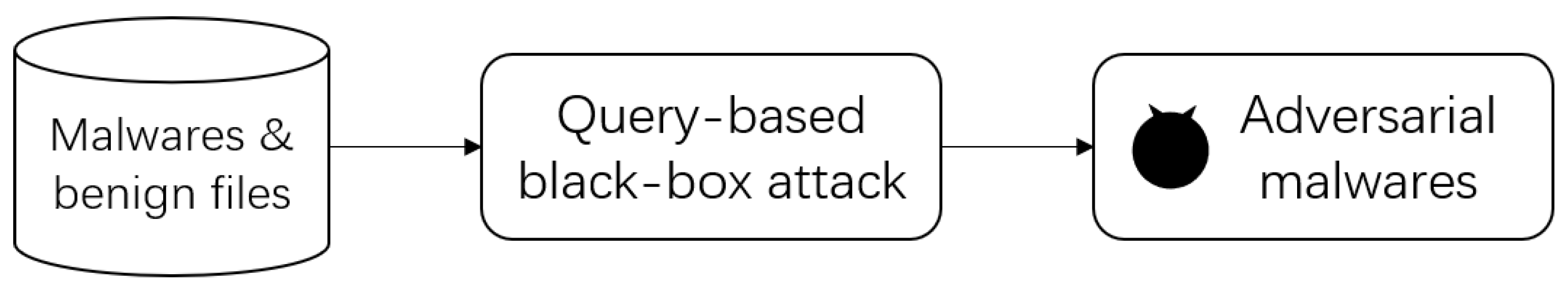
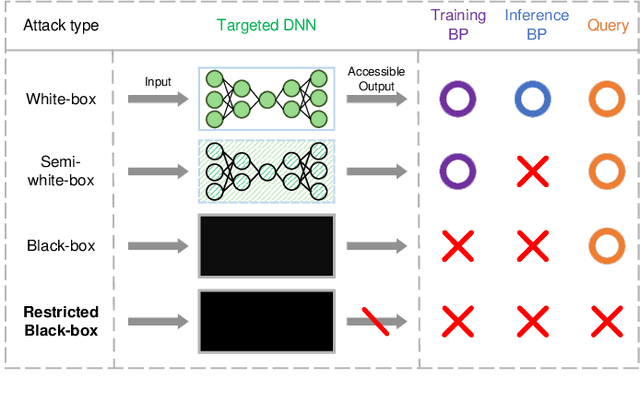
Electronics | Free Full-Text | MalDBA: Detection for Query-Based Malware Black-Box Adversarial Attacks
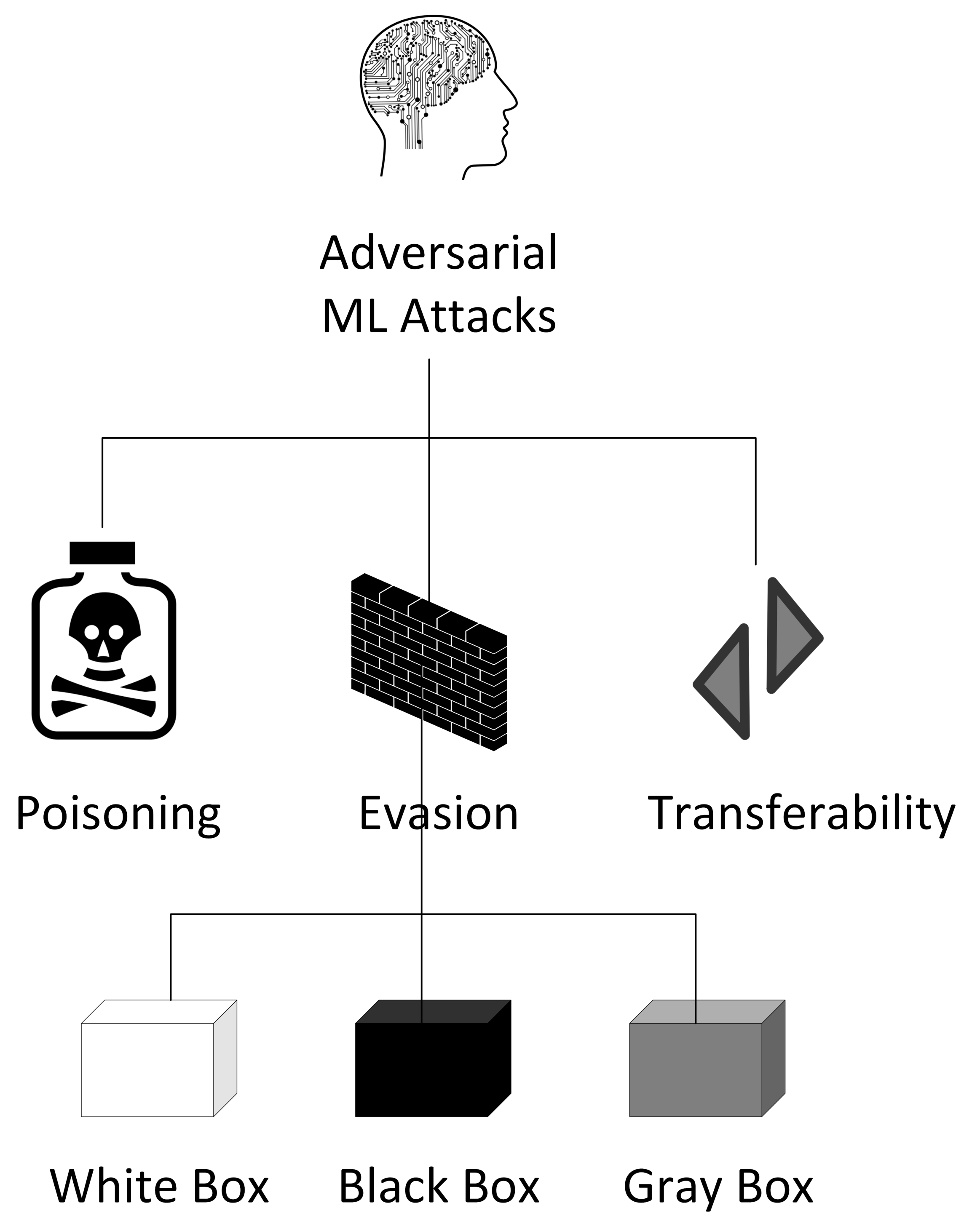
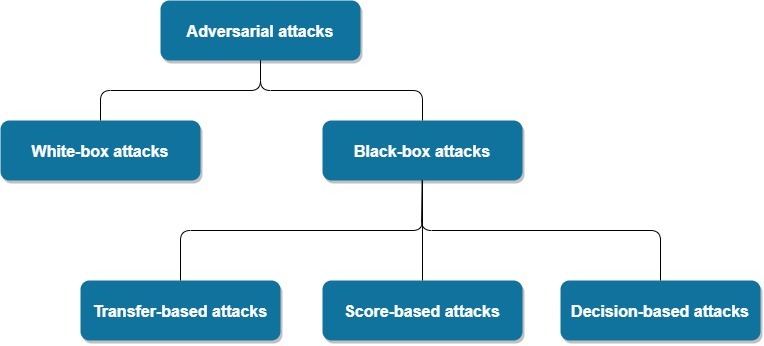
JCP | Free Full-Text | Functionality-Preserving Adversarial Machine Learning for Robust Classification in Cybersecurity and Intrusion Detection Domains: A Survey
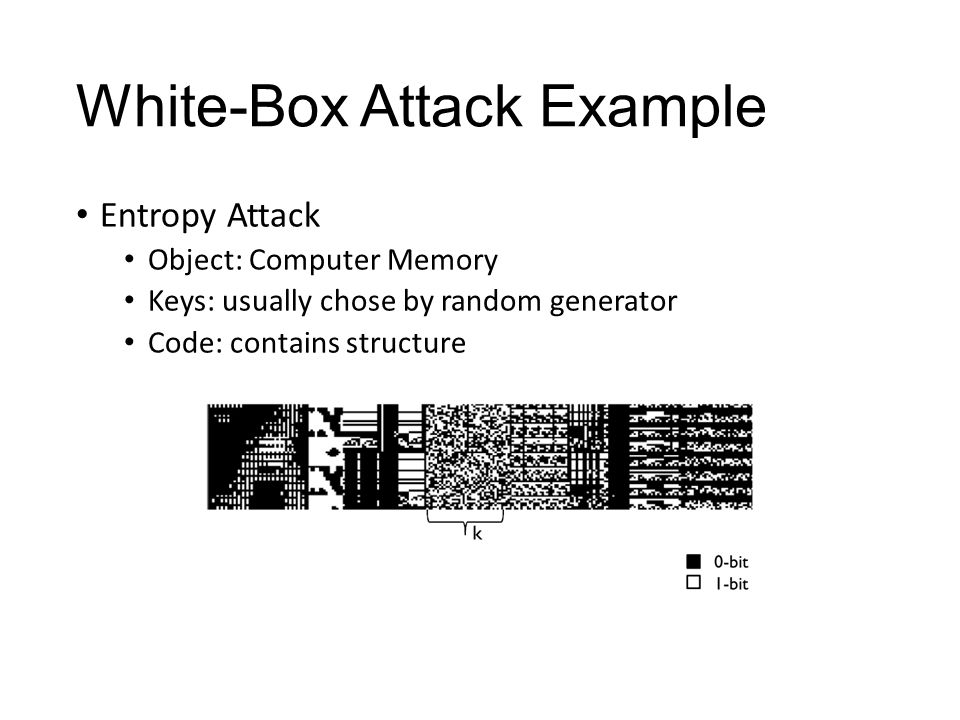
GitHub - demining/WhiteBox-Attack: We implement WhiteBox Attack on Bitcoin with differential errors according to the research scheme of Eli Biham and Adi Shamir to extract the secret key

Applied Sciences | Free Full-Text | Better Safe Than Never: A Survey on Adversarial Machine Learning Applications towards IoT Environment